In this blog post Manage Android BYOD with Microsoft Intune using Work Profile we will show how to protect company data on personal Android devices without taking over the whole phone. We’ll balance user privacy with strong security controls and give you practical steps you can follow today.
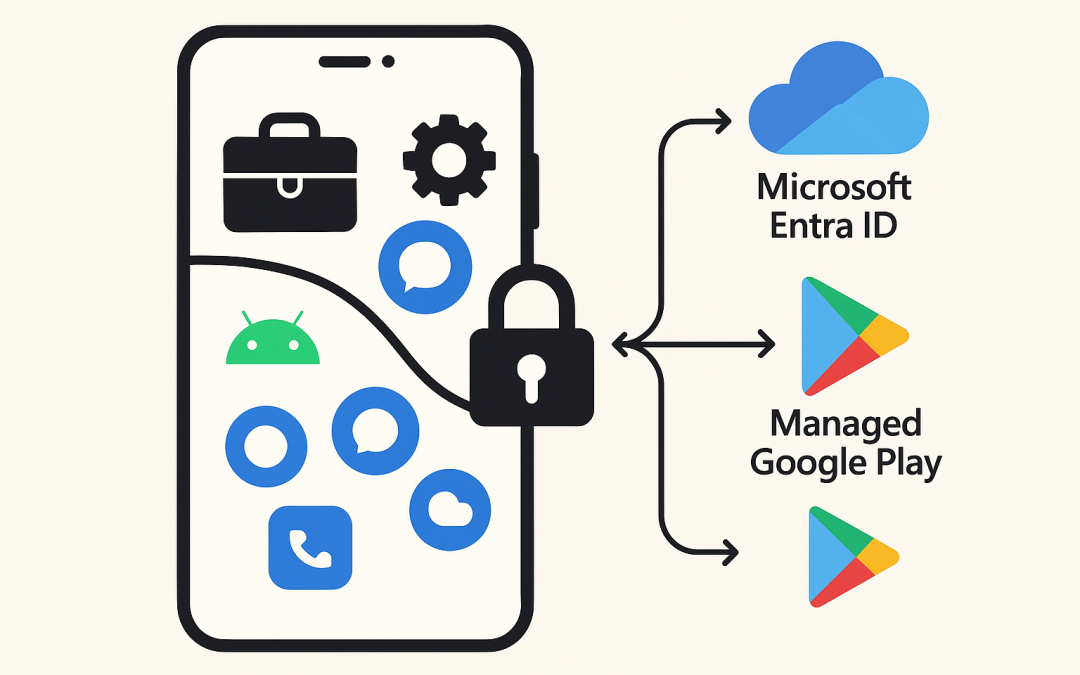
At a high level, Manage Android BYOD with Microsoft Intune using Work Profile uses Android Enterprise work profiles to separate work data and apps from personal data and apps. Microsoft Intune delivers policies and apps into the work side only, while Conditional Access ensures only healthy devices and protected apps reach corporate resources.
How the technology works
The core pieces are:
- Android Enterprise Work Profile: Creates a sandboxed “work” container on a personal device. IT manages only the work container; the personal side remains private.
- Microsoft Intune: Cloud-based endpoint management that pushes apps, compliance rules, and configuration to the work profile, and enforces data protection with App Protection Policies.
- Microsoft Entra ID (formerly Azure AD): Provides identity, device compliance signals, and Conditional Access to gate corporate resources.
- Managed Google Play: Enterprise app store for the work profile. You approve and assign apps; users install them into the work side only.
When a user enrolls a personal Android device (Android 8.0+ recommended), Intune activates a work profile. Apps you approve in Managed Google Play appear in the work profile, marked with a briefcase icon. Intune applies compliance and configuration to the work side, while App Protection Policies control data flow within managed apps. Conditional Access then permits access to Exchange, SharePoint, Teams, and other resources only when the device and apps meet your standards.
Before you start
- Licensing: Microsoft Intune (included in many Microsoft 365 plans), and Microsoft Entra ID.
- Admin access: Intune admin center and Entra admin center.
- Devices: Android 8.0 or later for a modern, supported experience.
- Decide management mode: Work profile (MDM + MAM) vs. App Protection only (MAM without enrollment). This guide focuses on work profile.
Quick architecture view
- User signs in to the Company Portal, which triggers creation of a work profile on the device.
- Intune pushes policies to the work profile and publishes apps via Managed Google Play.
- Device reports compliance to Intune, which syncs to Entra ID.
- Conditional Access checks: compliant device and/or protected app required for resource access.
Step-by-step setup in Intune
1) Connect Intune to Managed Google Play
- In Intune admin center: Tenant administration > Connectors and tokens > Managed Google Play.
- Sign in with a corporate Google account to establish the connection.
This enables you to approve Android Enterprise apps and make them available in the work profile.
2) Allow personally owned work profile enrollment
- Go to Devices > Android > Android enrollment.
- Ensure “Personal devices with work profile” is allowed. Use enrollment restrictions to block legacy Device Administrator and require work profile.
3) Create a compliance policy (Android Enterprise)
- Devices > Compliance policies > Create policy > Android Enterprise.
- Recommended settings:
- Block rooted devices.
- Require a device lock (PIN/biometric) on the device.
- Require a minimum OS version you support (e.g., Android 10+).
- Require Google Play Protect and encryption enabled.
- Set actions for noncompliance (e.g., mark as noncompliant immediately and send email after 1 day).
4) Configure device restrictions for the work profile
- Devices > Configuration > Create policy > Android Enterprise > Personally-owned work profile > Device restrictions.
- Common settings:
- Block screen capture in work profile (optional, balances UX and risk).
- Disable installation from unknown sources in the work profile.
- Disable USB file transfer from work profile (if data exfiltration is a concern).
- Require strong work profile password settings (separate from device lock if desired).
5) Approve and assign apps via Managed Google Play
- Apps > Android > Add > Managed Google Play app.
- Approve Microsoft apps (Outlook, Teams, OneDrive, Edge, Defender) and line-of-business apps if available in Google Play.
- Assign as Required (auto-installs in work profile) or Available (user installs from the work Play store).
6) Apply App Protection Policies (MAM)
- Apps > App protection policies > Create policy > Android.
- Target “Device types: Managed” for work profile users; optionally create another policy for “Unmanaged” devices used only with MAM.
- Recommended settings:
- Require app PIN/biometric.
- Encrypt app data and restrict backup.
- Control cut/copy/paste (e.g., allow between managed apps only).
- Save-as to OneDrive/SharePoint only; block personal storage.
- Wipe corporate data from apps after N days offline.
7) Enforce Conditional Access
- In Entra admin center: Security > Conditional Access > New policy.
- Scope cloud apps (e.g., Exchange Online, SharePoint, Teams).
- For BYOD work profile: Require “Device to be marked as compliant.”
- For MAM-only scenarios: Require “Approved client app” and “App protection policy.”
User experience
- User installs Microsoft Intune Company Portal from Google Play.
- Signs in with corporate credentials and accepts the work profile setup prompts.
- Android creates the work profile; a new work tab and briefcase icons appear.
- Required work apps install automatically; user can grab optional apps from the work Play store.
- Access to corporate email and files is granted once compliance is met.
Privacy note: IT can see and manage only the work profile. Personal apps, photos, texts, and location remain private. If the device is retired, only the work profile is removed.
Security best practices
- Pair compliance policies with Conditional Access to block noncompliant devices.
- Use App Protection Policies even on managed devices—defense in depth against data leaks.
- Deploy Microsoft Defender for Endpoint for mobile threat defense and integrate its risk level into Conditional Access.
- Block unknown sources and screen capture in the work profile if your data sensitivity demands it.
- Set device cleanup rules to automatically retire stale devices after inactivity.
Common pitfalls and how to avoid them
- No Managed Google Play connection: You won’t see Android Enterprise apps. Ensure the connector is set up and synced.
- Using legacy Device Administrator: Prefer Android Enterprise work profile; block Device Admin enrollment in restrictions.
- CA policy deadlocks: Exclude break-glass accounts and test with a pilot group before global deployment.
- Overly strict policies: Start with a report-only (audit) CA policy, then enforce once you confirm user impact.
- Missing end-user comms: Publish a short guide with screenshots so users know what to expect during enrollment.
Troubleshooting tips
- Company Portal > Help > Send logs; review the enrollment status page for errors.
- In Intune, check device compliance and policy assignment status under the device record.
- Ensure Google Play Services is up to date; outdated services can block work profile creation.
- If apps don’t appear, re-sync Managed Google Play apps in Intune.
Automate reporting with Microsoft Graph
You can query BYOD Android devices and compliance states with Microsoft Graph. Example PowerShell snippet:
# Requires Microsoft.Graph module
Install-Module Microsoft.Graph -Scope CurrentUser
Import-Module Microsoft.Graph
Connect-MgGraph -Scopes DeviceManagementManagedDevices.Read.All
# List personal Android devices and their compliance states
Get-MgDeviceManagementManagedDevice -All `
-Filter "operatingSystem eq 'Android' and managedDeviceOwnerType eq 'personal'" |
Select-Object userDisplayName, deviceName, complianceState, enrolledDateTime, azureADDeviceId
Use scheduled jobs to export reports for operations and security reviews.
Roll-out checklist
- Enable Managed Google Play connector.
- Create and assign Android Enterprise compliance policies.
- Create work profile device restriction policies.
- Approve and assign core apps (Outlook, Teams, OneDrive, Edge, Defender).
- Publish App Protection Policies and test copy/paste, save-as, and PIN prompts.
- Enable Conditional Access in report-only, then enforce after testing.
- Prepare end-user communication and support FAQs.
- Pilot with a small group; iterate; then scale to production.
Conclusion
Android BYOD with Microsoft Intune and work profiles gives you the best of both worlds: strong, enforceable data protection for the business and clear privacy boundaries for your people. With Managed Google Play, compliance policies, App Protection, and Conditional Access working together, you can deploy fast, scale confidently, and keep corporate data safe without locking down personal devices.
If you’d like help planning or executing a BYOD rollout, our team at CloudProinc.com.au works with organisations of all sizes to design secure, user-friendly mobile programs.